在此网站下载需要版本的安装包:https://slproweb.com/products/Win32OpenSSL.html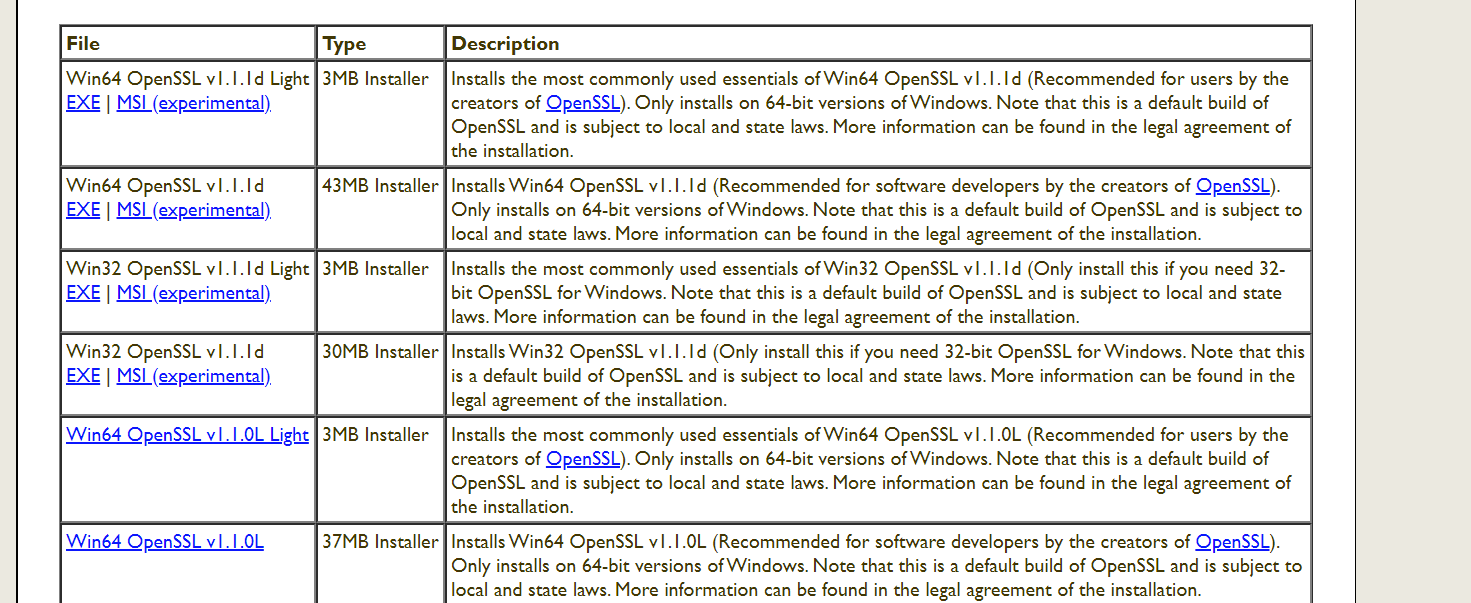
安装过程不再介绍,在其中一个选项,选择将 openssl 安装到 /bin。
将 安装目录中的 /bin/openssl.exe 添加到系统 PATH 中,参考:https://niekun.net/index.php/archives/413.html
测试命令是否生效: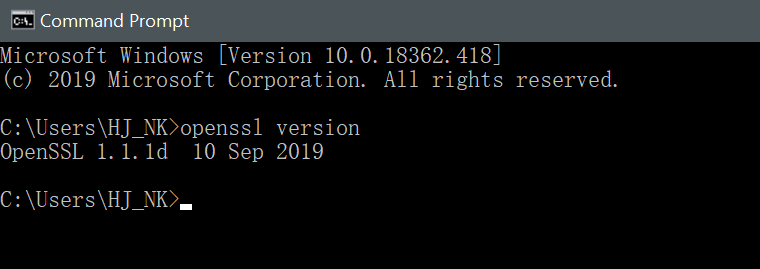
需要用到的工具:
Linux
MySQL
openssl
gdrive
crontab
脚本实现定时自动备份数据库及指定目录文件夹,备份文件加密处理,自动上传到google drive。可设定备份文件保留天数。
脚本下载,设定权限:
wget --no-check-certificate https://github.com/teddysun/across/raw/master/backup.sh
chmod +x backup.sh修改脚本配置 具体参考:https://teddysun.com/469.html
安装 openssl 参考:https://niekun.net/index.php/archives/449.html
安装 gdrive 参考:https://niekun.net/index.php/archives/460.html
设置 crontab 定时 参考:https://niekun.net/index.php/archives/461.html
]]>openssl 安装参考:https://niekun.net/index.php/archives/183.html
三个部分组成:
libcryto:这是一个具有通用功能的加密库,里面实现了众多的加密库
libssl,这个是实现ssl机制的,它是用于实现TLS/SSL的功能
openssl,是个多功能命令行工具,它可以实现加密解密,甚至还可以当CA来用,可以让你创建证书、吊销证书
marconie@marco-mbp ~ % openssl help
Standard commands
asn1parse ca ciphers cms
crl crl2pkcs7 dgst dhparam
dsa dsaparam ec ecparam
enc engine errstr gendsa
genpkey genrsa help list
nseq ocsp passwd pkcs12
pkcs7 pkcs8 pkey pkeyparam
pkeyutl prime rand rehash
req rsa rsautl s_client
s_server s_time sess_id smime
speed spkac srp storeutl
ts verify version x509
Message Digest commands (see the `dgst' command for more details)
blake2b512 blake2s256 gost md4
md5 mdc2 rmd160 sha1
sha224 sha256 sha3-224 sha3-256
sha3-384 sha3-512 sha384 sha512
sha512-224 sha512-256 shake128 shake256
sm3
Cipher commands (see the `enc' command for more details)
aes-128-cbc aes-128-ecb aes-192-cbc aes-192-ecb
aes-256-cbc aes-256-ecb aria-128-cbc aria-128-cfb
aria-128-cfb1 aria-128-cfb8 aria-128-ctr aria-128-ecb
aria-128-ofb aria-192-cbc aria-192-cfb aria-192-cfb1
aria-192-cfb8 aria-192-ctr aria-192-ecb aria-192-ofb
aria-256-cbc aria-256-cfb aria-256-cfb1 aria-256-cfb8
aria-256-ctr aria-256-ecb aria-256-ofb base64
bf bf-cbc bf-cfb bf-ecb
bf-ofb camellia-128-cbc camellia-128-ecb camellia-192-cbc
camellia-192-ecb camellia-256-cbc camellia-256-ecb cast
cast-cbc cast5-cbc cast5-cfb cast5-ecb
cast5-ofb des des-cbc des-cfb
des-ecb des-ede des-ede-cbc des-ede-cfb
des-ede-ofb des-ede3 des-ede3-cbc des-ede3-cfb
des-ede3-ofb des-ofb des3 desx
idea idea-cbc idea-cfb idea-ecb
idea-ofb rc2 rc2-40-cbc rc2-64-cbc
rc2-cbc rc2-cfb rc2-ecb rc2-ofb
rc4 rc4-40 seed seed-cbc
seed-cfb seed-ecb seed-ofb sm4-cbc
sm4-cfb sm4-ctr sm4-ecb sm4-ofbmarconie@marco-mbp ~ % openssl enc -help
Usage: enc [options]
Valid options are:
-help Display this summary
-list List ciphers
-ciphers Alias for -list
-in infile Input file
-out outfile Output file
-pass val Passphrase source
-e Encrypt
-d Decrypt
-p Print the iv/key
-P Print the iv/key and exit
-v Verbose output
-nopad Disable standard block padding
-salt Use salt in the KDF (default)
-nosalt Do not use salt in the KDF
-debug Print debug info
-a Base64 encode/decode, depending on encryption flag
-base64 Same as option -a
-A Used with -[base64|a] to specify base64 buffer as a single line
-bufsize val Buffer size
-k val Passphrase
-kfile infile Read passphrase from file
-K val Raw key, in hex
-S val Salt, in hex
-iv val IV in hex
-md val Use specified digest to create a key from the passphrase
-iter +int Specify the iteration count and force use of PBKDF2
-pbkdf2 Use password-based key derivation function 2
-none Don't encrypt
-* Any supported cipher
-rand val Load the file(s) into the random number generator
-writerand outfile Write random data to the specified file
-engine val Use engine, possibly a hardware deviceopenssl enc -aes-256-cbc -md sha512 -pbkdf2 -iter 1000 -pass pass:PASSWORD -in YOURFILE -out ENC_YOURFILE
openssl enc -aes-256-cbc -d -md sha512 -pbkdf2 -iter 1000 -pass pass:PASSWORD -in YOURFILE -out ENC_YOURFILE
注意:如果主机性能较低,建议去掉自定义 iter 使用 pbkdf2 默认设置即可。
]]>在此网站下载需要版本的安装包:https://slproweb.com/products/Win32OpenSSL.html
安装过程不再介绍,在其中一个选项,选择将 openssl 安装到 /bin。
将 安装目录中的 /bin/openssl.exe 添加到系统 PATH 中,参考:https://niekun.net/index.php/archives/413.html
测试命令是否生效:
This tutorial shows you how to set up strong SSL security on the nginx webserver. We do this by updating OpenSSL to the latest version to mitigate attacks like Heartbleed, disabling SSL Compression and EXPORT ciphers to mitigate attacks like FREAK, CRIME and LogJAM, disabling SSLv3 and below because of vulnerabilities in the protocol and we will set up a strong ciphersuite that enables Forward Secrecy when possible. We also enable HSTS and HPKP. This way we have a strong and future proof ssl configuration and we get an A+ on the Qually Labs SSL Test.
本文使用的配置需要相关软件的最低版本要求:
Nginx: 1.13.0 -- 升级教程:https://niekun.net/index.php/archives/30.html
openssl: 1.0.1 -- 升级教程:https://niekun.net/index.php/archives/183.html
首先需要生成一个 4096 bit 的 DH parameters:
openssl dhparam -out /etc/nginx/your.domain/dhparam.pem 4096
编辑 Nginx 配置文件,在server段加入或修改如下:
ssl_protocols TLSv1 TLSv1.1 TLSv1.2 TLSv1.3;
ssl_prefer_server_ciphers on;
ssl_ciphers ECDHE-RSA-AES256-GCM-SHA512:DHE-RSA-AES256-GCM-SHA512:ECDHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-SHA384;
ssl_dhparam /etc/nginx/your.domain/dhparam.pem;
ssl_ecdh_curve secp384r1;
ssl_session_timeout 10m;
ssl_session_cache shared:SSL:10m;
ssl_session_tickets off;
ssl_stapling on;
ssl_stapling_verify on;
resolver 8.8.8.8 1.1.1.1 valid=300s;
resolver_timeout 5s;
add_header Strict-Transport-Security "max-age=63072000; includeSubDomains; preload";
add_header X-Frame-Options DENY;
add_header X-Content-Type-Options nosniff;
add_header X-XSS-Protection "1; mode=block";需要注意的是,设置ssl_stapling on 的情况下,如果证书签发的域名无法被正确的解析,会导致 nginx 启动很慢最终导致 timeout 报错。
ssl_ciphers 的设置可能会影响一些老版本系统或浏览器的访问,以下是兼容 IE6/WinXP 的配置:
EECDH+AESGCM:EDH+AESGCM:ECDHE-RSA-AES128-GCM-SHA256:AES256+EECDH:DHE-RSA-AES128-GCM-SHA256:AES256+EDH:ECDHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-SHA384:ECDHE-RSA-AES128-SHA256:ECDHE-RSA-AES256-SHA:ECDHE-RSA-AES128-SHA:DHE-RSA-AES256-SHA256:DHE-RSA-AES128-SHA256:DHE-RSA-AES256-SHA:DHE-RSA-AES128-SHA:ECDHE-RSA-DES-CBC3-SHA:EDH-RSA-DES-CBC3-SHA:AES256-GCM-SHA384:AES128-GCM-SHA256:AES256-SHA256:AES128-SHA256:AES256-SHA:AES128-SHA:DES-CBC3-SHA:HIGH:!aNULL:!eNULL:!EXPORT:!DES:!MD5:!PSK:!RC4;修改完成后测试配置及重启:
service nginx configtest
service nginx reload
service nginx restart
可以在这里测试网站安全级别,最高为 A+: https://www.ssllabs.com/ssltest/index.html
]]>Linux 下从源码编译教程参考:https://blog.niekun.net/archives/883.html
使用 http2 和 tls1.3 需要升级到最新版 1.1.1的 openssl,所以本文介绍如何下载及编译最新版。
下载最新版 1.1.1b:
wget https://www.openssl.org/source/openssl-1.1.1b.tar.gz
解压及进入目录:
tar -zxf openssl-1.1.1b.tar.gz && cd openssl-1.1.1b
建立安装文件夹及软链接:
mkdir /opt/openssl-1.1.1b
ln -s /opt/openssl-1.1.1b /opt/openssl
解析config:
./config --prefix=/opt/openssl-1.1.1b
安装编译器及执行 make:
apt-get install make gcc
make
测试是否有错误:
make test
备份当前的 openssl 文件:
mv /usr/bin/openssl ~/tmp
开始安装:
make install
link 新安装的文件到默认执行地址:
ln -s /opt/openssl/bin/openssl /usr/bin/openssl
刷新 link 及缓存:
ldconfig
查看当前 openssl 版本:
openssl version
如果显示:OpenSSL 1.1.1b 字样则表示安装成功。
]]>